In Q3 FY26, Salesforce reported more than $540M in Agentforce ARR, 330% year-on-year growth, and over 9,500 paid Agentforce deals in production, processing trillions of tokens per quarter (Source). At that scale, a single misconfigured or compromised agent is no longer “one bad bot”. It’s a systemic risk to revenue, brand, and compliance. Traditional monitoring tools were built to tell you when a server is slow, not why an AI agent decided to show a private opportunity record to the wrong user. They track symptoms, not reasoning.
Salesforce’s Agentforce Observability is a response to this gap: a “mission control” that enables IT and business teams to see every interaction, trace every decision, and tune every agent in near-real time. The security opportunity is clear. Combine this deep visibility with Zero Trust and modern identity protection, and CRM becomes the best-governed system in your stack.
From Monitoring to Observability: What Leaders Actually Get
Most leaders still hear "observability" and think of fancier dashboards. That’s not what Agentforce Observability is.
Monitoring answers: “Is something broken?” It operates on static metrics and thresholds (error rates, latency, uptime) and was designed for predictable infrastructure. Useful, but blind to the real question in an AI-first CRM: “Why did the agent do that?”
Observability answers: “What exactly happened, why, and should we trust it?” It combines logs, metrics, and traces so you can replay every agent session, see the reasoning path, and pinpoint failure points. In Agentforce, that shows up as three concrete capabilities:
- Agent Analytics – Aggregated KPIs for all agents: sessions, success/deflection rates, latency, top topics, and adoption, across orgs and clouds.
- Agent Optimization – Deep session-level tracing with intent tags, sentiment, topic clustering, and Quality Scores so teams can drill into specific turns in a conversation and see misinterpretations and configuration gaps.
- Agent Health Monitoring – Near real-time alerts on responsiveness, errors, and anomalies tied to business KPIs, enabling immediate interventions on agent configs and flows.
For security and risk leaders, the distinction is crucial.
Monitoring tells you an Agentforce service is up; observability tells you that one agent handled 1,200 refund requests in an hour from a single IP range, and most of them bypassed standard checks.
The Security Challenge of Modern Salesforce Environments
Today, the security problem isn’t “we moved to SaaS”; it’s “our SaaS is now run by autonomous software.”
Three macro trends matter inside Salesforce:
- Machine identities have exploded. Across enterprises, machine identities now outnumber humans by roughly 82:1, and that ratio is growing as organizations spin up fleets of AI agents and integrations. Each of those identities carries API keys, OAuth tokens, and object permissions that attackers can abuse.
- Attacks are shifting from users to agents and builders. 2025 saw over 8,000 reported breaches and hundreds of AI-related incidents where the root cause involved misused credentials, API abuse, or misconfigured AI components, not classic CVEs. Threat actors are explicitly targeting developers and low-code builders because compromising them lets attackers poison agents at the source.
- Prompt injection and tool misuse are now mainstream. OWASP’s 2025 GenAI list ranks prompt injection as LLM01, the top risk, because a single crafted input can turn a helpful agent into a data-exfiltration pipeline. In a CRM context, that could be a “note” or “address” field that quietly instructs an agent to dump account data into an attacker-controlled destination.
Salesforce environments amplify that risk surface: deep customer data, payment journeys, support histories, and embedded AI across Sales, Service, Marketing, and custom Experience Cloud flows. Without observability, an abused agent looks just like a productive one: lots of activity, few errors, satisfied logs.
How Salesforce Agentforce Observability Empowers Enterprise Security
Agentforce Observability is designed to address the “black box” issue that the Salesforce team openly highlights in the Agentforce 360 lifecycle. The three pillars of the Agentforce Observability include:
Agent Analytics
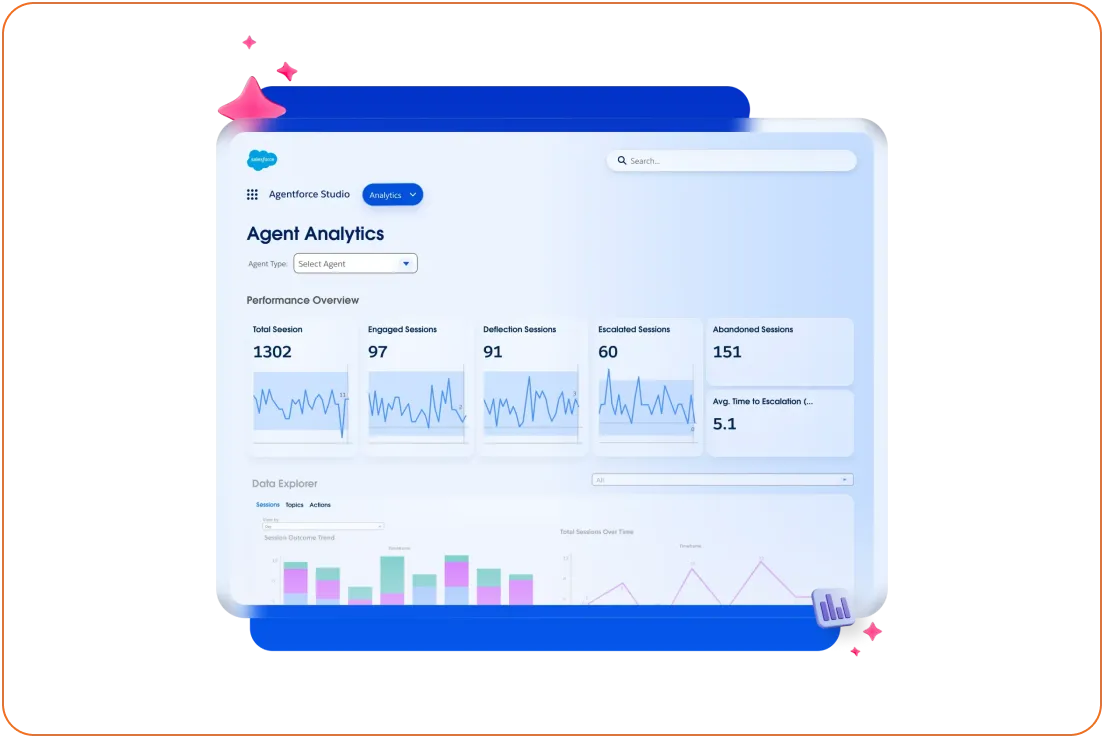
Agent Analytics gives a consolidated view of all agents across orgs, business units, and clouds, with usage, effectiveness, and business KPIs in one place. For security teams, that means:
Agent Analytics gives a consolidated view of all agents across orgs, business units, and clouds, with usage, effectiveness, and business KPIs in one place. For security teams, that means:
- Spotting agents whose behavior suddenly diverges from historical patterns (e.g., unusual spikes in sensitive-object access).
- Identifying topics and flows that consistently lead to escalations or errors, which often hide policy or configuration gaps.
Agent Optimization
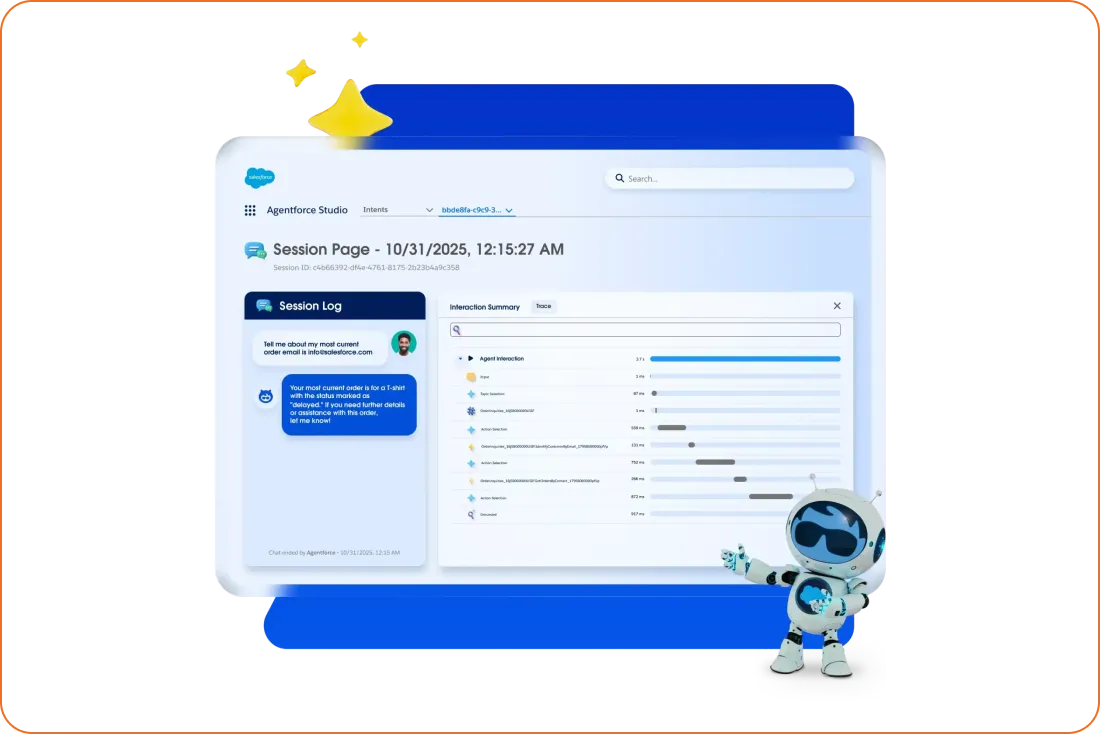
Agent Optimization is where observability crosses into security engineering. Salesforce’s Session Tracing Data Model logs every input, output, reasoning step, LLM call, tool invocation, and guardrail check, storing them in Data 360 as structured, queryable data. Combined with Quality Scores, intent tags, and sentiment, teams can:
- Replay suspicious conversations and review each turn to understand why the agent made the decision.
- Cluster sessions where the agent misinterpreted instructions or bypassed expected checks, then correlate those with permissions, topics, or data sources.
- Use “bad session clusters” as training material to harden prompts, flows, and guardrails, reducing both operational risk and security exposure.
Agent Health Monitoring
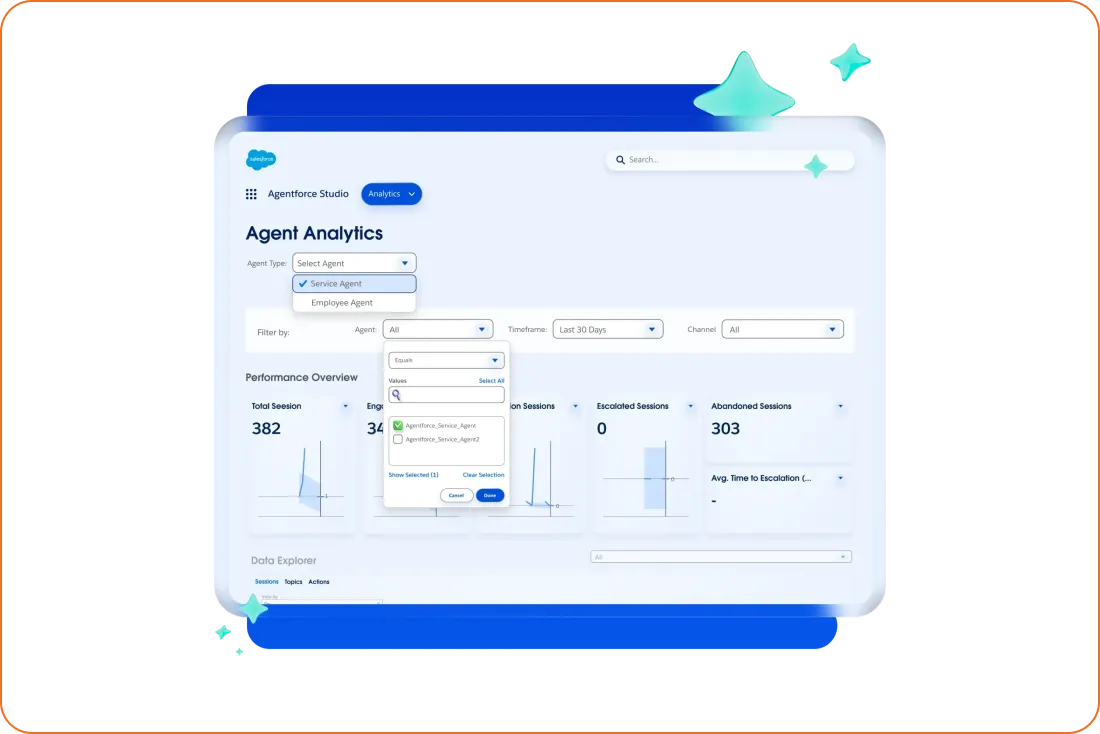
Finally, Agent Health Monitoring provides continuous visibility into uptime, latency, errors, and failure signatures, tied directly to agent business logic. Health monitoring becomes a security control when leaders configure:
- Alerts on anomalous spikes in particular intents (e.g., “export,” “refund,” “update permissions”).
- Error or escalation patterns that correlate with specific geographies, IP ranges, or integration partners (useful for spotting API abuse or supply-chain issues).
Salesforce is rolling this out as a GA capability through 2026 with regional support, making it a core part of Agentforce Studio rather than an add-on tool.
Real-world Security Use Cases Inside Salesforce
Done right, Agentforce Observability changes how you answer three uncomfortable questions every exec is now asking.
“How would we know if an AI agent was quietly leaking data?”
With session-level tracing, you can query for patterns like: “show all sessions where this agent accessed more than N records in M minutes and responses included unusual fields.”
Combined with Quality Scores and clustering, you can identify sessions where the agent was technically “helpful” but contextually suspicious.
“Can we distinguish fraud-like behavior from legitimate surge?”
In a Salesforce org where an Agentforce-powered chatbot handles payment disputes, Agent Analytics and Optimization let you:
- Tag intents such as “chargeback,” “refund,” or “address change.”
- Create anomaly rules for sudden bursts in those intents from specific user segments or channels.
- Trace those sessions to see whether the agent followed policy (e.g., verified identity, checked historical behavior) before executing actions.
“Can we actually investigate incidents at ‘agent speed’?”
In a traditional breach, correlating identity logs, API logs, and app logs takes days. With Agentforce Observability, most of that context is already stitched together in the Session Tracing Data Model and can be piped into your SIEM/SOAR.
Security teams can move from “find every log line for user X across five systems” to “replay every Agentforce session for user X in the last 48 hours, enriched with identity, geography, and data-sensitivity tags” - then trigger automated containment workflows if needed.
Best Practices to Implement Observability for Salesforce Security
Leaders who want real risk reduction and not just a dashboard should anchor on five practical moves:
- Turn on session tracing and central logging in Data 360 from day one. Make observability part of the Agentforce rollout checklist, not a phase-two idea.
- Instrument business-aware guardrails and tags. Use intent tags, sentiment, and Quality Scores as first-class signals for security and compliance, not just CX tuning.
- Align health alerts with Zero Trust policies. Don’t just alert on latency; alert when agents touch sensitive objects outside of expected flows, or when they invoke tools they rarely use. Pair these with automatic playbooks in your SIEM/SOAR.
- Integrate observability with identity protection. Treat every agent as an identity: use short-lived credentials, least-privilege roles, and continuous, behavior-based access evaluation.
- Create a joint AI Governance pod. Put Security, Salesforce CoE, Data, and Business Ops around the same table reviewing observability insights weekly: which agents to scale, which to retrain, which to constrain.
The Future: Zero Trust, but For Agents
Zero Trust has already crossed the chasm. Over 80% of enterprises are implementing it, with many reporting double-digit reductions in incidents and strong ROI. The next frontier is Zero Trust for AI agents inside systems like Salesforce.
That future looks like this:
- Every agent is treated as an identity with a governed scope and continuously verified behavior.
- Observability data feeds AI-driven anomaly detection that can predict and prevent rogue behavior, not just react to it.
- Agent development lifecycles (like Salesforce’s four-stage Agentforce 360 model) include security and observability as first-class stages alongside build, integrate, and execute.
As a Salesforce Summit Partner with deep experience in complex, multi-cloud CRM programs, iOPEX helps enterprises turn Agentforce Observability from “powerful feature” into an operational discipline woven into how sales, service, and security actually run.
Working alongside Salesforce and your internal teams, iOPEX designs
- Zero Trust–aligned data models
- Implements session tracing and analytics in Data Cloud
- Integrates observability signals into your existing SIEM/SOAR stack
- Codifies AI governance across IT, security, and business stakeholders.
This isn't a one-time implementation. iOPEX's Intelligence as a Service model provides continuous observability engineering, governance tuning, and optimization as your Agentforce deployment scales. The result: secure, explainable AI agents that your board trusts and your customers never have to question.
Ready to make observability operational? iOPEX helps enterprises deploy Agentforce with security, speed, and confidence. Talk to our team to design your observable AI strategy today!










